A Paradigm Shift in Cyber Defense
Cyber crime is growing exponentially. Traditional security solutions are no longer up to the task of protecting our ever-changing, hybrid and modern data environments. Organisations have historically invested heavily in perimeter-centric security, in an attempt to keep malicious actors ‘out’. Traditional cyber security focuses on preventing breaches. However, the total prevention of breaches has proved simply too illusive. Securing the perimeter against cyber incursions is no longer adequate on its own.
No Longer a Matter of ‘if’ but Rather ‘When’
While there may still be some reluctance amongst IT security teams in openly admitting that cyber security breaches are inevitable, most now recognise that breaches of the perimeter defenses are unavoidable. Even worse are the statistics when it comes to breach identification. IBM advise that the average time to identify a breach is 207 days. That’s a considerable amount of time for malicious actors to patiently move - from system to system - in search of a valuable target. The average cost of a data breach in 2021 was also a staggering $4.24M. Thus, organisations need a new approach to cyber threat mitigation. One that cohesively and efficiently realises network virtualisation and enables the micro-segmentation of systems.
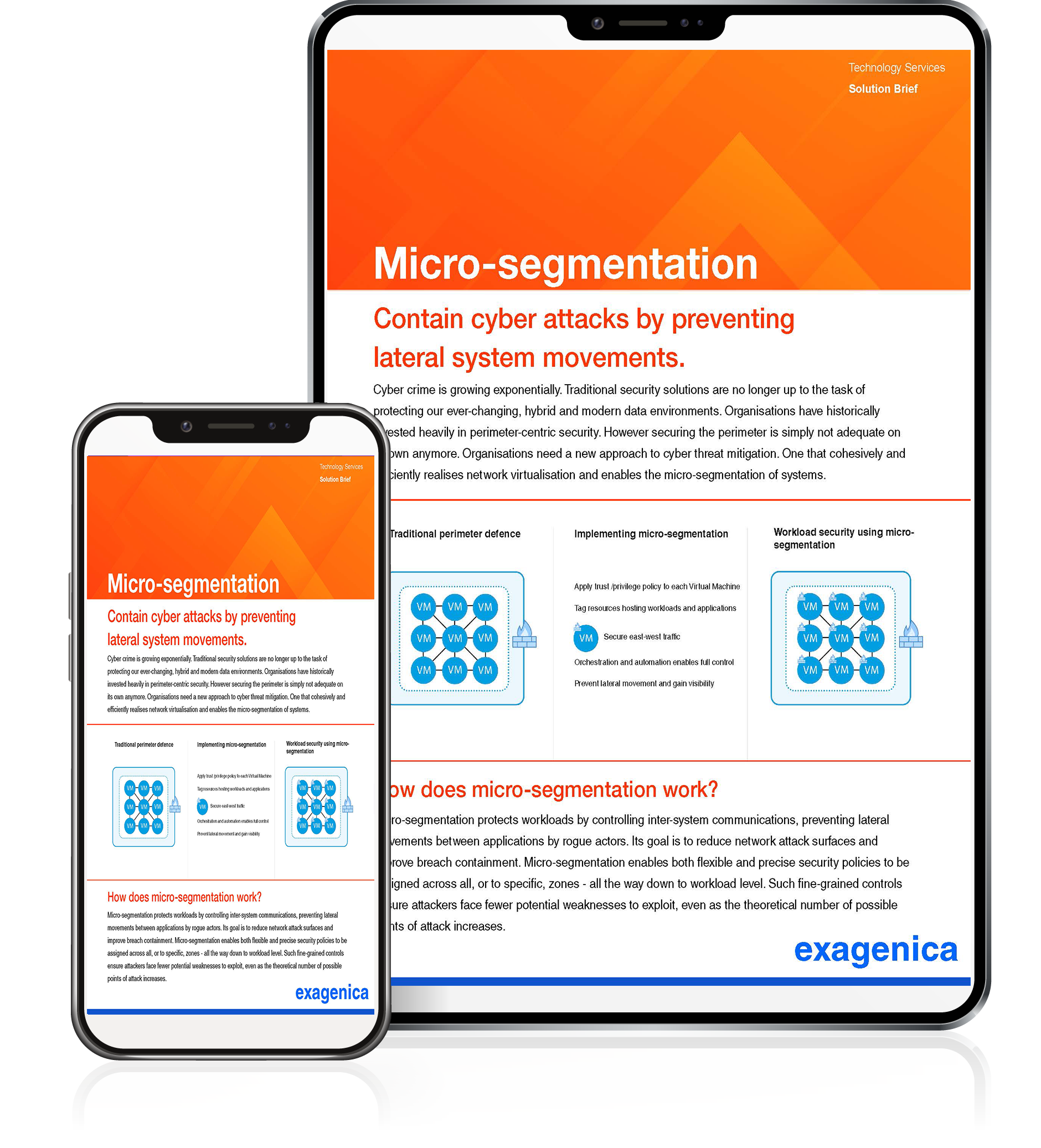
How Does Micro-Segmentation Work?
Micro-segmentation protects workloads by controlling inter-system communications, preventing lateral movements between applications by rogue actors. Its goal is to reduce network attack surfaces and improve breach containment. Micro-segmentation enables both flexible and precise security policies to be assigned across all zones, or to specific zones - all the way down to workload level. Such fine-grained controls ensure attackers face fewer potential weaknesses to exploit, even as the theoretical number of possible points of attack increases.
MICRO-SEGMENTATION LETS YOU:
- Secure and control application traffic at every workload.
- Implement a compensating control for applications and workloads that cannot be patched.
- Ensure consistent and continuous protection that automatically adapts to changes (e.g. movement of workloads or new capacity across application environments).
- Enable AES-256 IPsec encryption for data in motion between a mix of Windows/Linux workloads or Windows/Linux workloads and VPN concentrators - with a single click and without additional hardware or custom software.